TL;DR
Infostealers are lightweight malware built to lift credentials, session cookies/tokens, browser-stored data, crypto wallets, and files and ship them to criminals within minutes. They’re sold as malware‑as‑a‑service (MaaS) and feed a wider economy of initial access brokers (IABs) and ransomware‑as‑a‑service (RaaS). Most infections start on personal, unmanaged devices via phishing, poisoned downloads, malvertising, or cracked software and then pivot into work accounts through BYOD.
If you’re someone who’s serious about keeping your digital life secure, you’ve probably heard of ransomware or phishing scams. But there’s a quieter, sneakier threat making waves in the cybercrime world: infostealers.
These malicious programs are like digital spies, slipping onto your devices to steal everything from your passwords to your crypto wallet keys. In 2023, Constella Intelligence reported over 500 million devices infected with infostealers, resulting in nearly 2 billion stolen records. That’s a wake-up call for anyone who values their privacy!
In this deep dive, we’ll unpack what infostealers are, how they operate, and why they’re a cornerstone of modern cybercrime. More importantly, we’ll arm you with practical, actionable steps to protect yourself, whether you’re a casual internet user or a cybersecurity enthusiast. Let’s get started and lock down your digital world!
What Are Infostealers?
Infostealers are malicious programs designed to snatch sensitive data from your devices and send it straight to cybercriminals. Think of them as digital pickpockets, silently grabbing your login credentials, credit card details, and even personal files. That’s a staggering amount of compromised data!
These malware variants target a wide range of information, including:
- Login credentials: Usernames, email addresses, and passwords.
- Financial data: Credit card numbers, bank account details, and cryptocurrency wallet keys.
- Personal info: Social Security numbers, addresses, and phone numbers.
- Browser data: Cookies, browsing history, and saved form data.
- Files and communications: Documents, emails, and chat logs.
- Screenshots: Some infostealers capture what’s on your screen at key moments.
Infostealers have evolved from their roots in banking trojans like ZeuS, which leaked its source code in 2011, sparking a surge in customized variants. Today, they’re a thriving part of the cybercrime economy, often sold as Malware-as-a-Service (MaaS) for as little as $120-$250 a month. This accessibility means even non-techy criminals can deploy them, making infostealers a growing threat in 2025.
Why You Should Care About Infostealers Now
Ransomware grabs headlines; infostealers make those headlines possible. Think of an infostealer as a credential vacuum: it lands quietly, copies anything that can get an attacker into your accounts, and phones home.
The logs it creates—usernames and passwords, session cookies, autofill data, tokens, wallet keys, screenshots—are bundled and sold in real time on underground markets and Telegram bots.
Those logs are then converted into VPN logins, cloud admin access, or corporate footholds. In many big incidents, investigators later find that stolen credentials showed up in stealer logs weeks or months earlier.
Two more reasons this matters in 2025:
- Lower barrier to entry. You no longer need to write malware. Affiliates rent strains like Lumma, RedLine, StealC, Vidar, Raccoon, and others through MaaS dashboards with one‑click campaigns.
- Personal devices drive risk. Research shows a large majority of stealer infections hit personal endpoints first. When those devices sync browsers or use saved passwords, corporate SaaS is one cookie away.
How Infostealers Work
Infostealers are stealthy and efficient, operating in a multi-step process to compromise your data. Here’s a breakdown of their playbook:
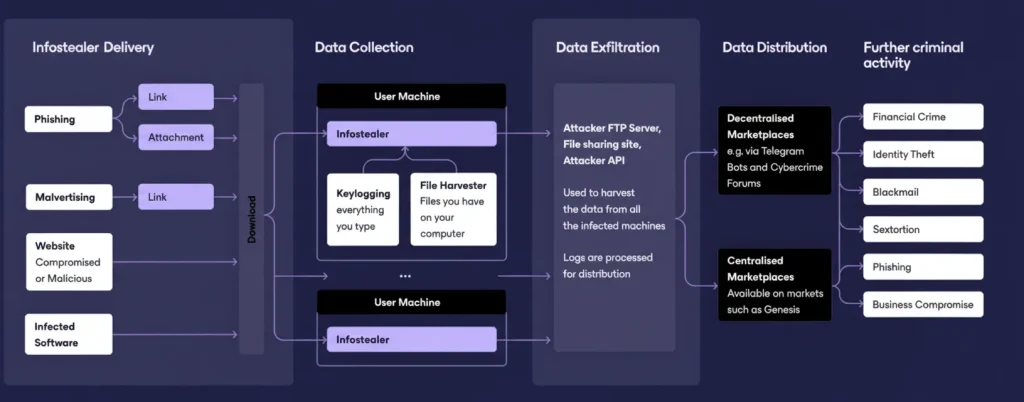
1. Delivery: Getting Onto Your Device
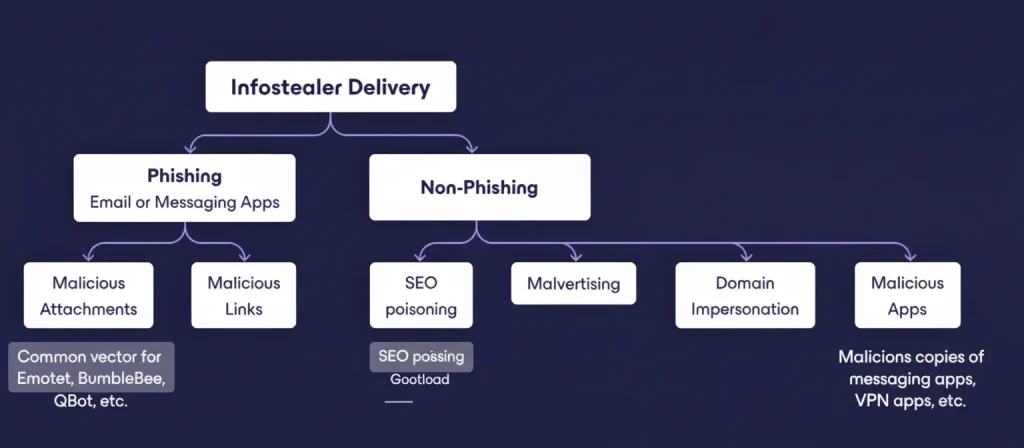
Infostealers sneak onto your system through various infection vectors:
- Phishing emails/texts: These often impersonate trusted brands or contacts, tricking you into clicking malicious links or downloading infected attachments. For example, a fake email from your bank might prompt you to open a file that installs the malware.
- Malicious websites: Visiting a compromised site or one designed to exploit browser vulnerabilities can trigger a “drive-by download” that installs the infostealer without your knowledge.
- Malvertising: Cybercriminals inject malicious ads into legitimate websites or hijack social media accounts to spread malware-laden ads.
- Cracked software or game mods: Downloading “free” versions of popular software or game cheats (like those for Hamster Kombat) often hides infostealers. ESET researchers found Lumma Stealer hidden in GitHub repositories posing as game bots.
- Social scams: Enticing social media posts or ads promising exclusive deals or content can lead to malware installation.
2. Data Collection: Raiding Your Device
Once installed, infostealers use a variety of techniques to harvest your data:
- Keylogging: Records every keystroke, capturing passwords, credit card numbers, and more.
- Form grabbing: Intercepts data entered into web forms before it’s encrypted, snagging login credentials and payment details.
- Clipboard hijacking: Monitors and alters clipboard content, stealing things like copied account numbers or crypto addresses.
- Browser session hijacking: Steals cookies and session tokens to bypass authentication, even multi-factor authentication (MFA). Variants like RacoonStealer excel at this.
- File harvesting: Scans your device for sensitive files, emails, or chat logs.
- Crypto wallet harvesting: Targets software like MetaMask to steal private keys, allowing attackers to drain your cryptocurrency.
- Screen captures: Takes screenshots to grab sensitive info displayed on your screen.
3. Data Exfiltration: Sending Your Info to the Bad Guys
The stolen data is quickly sent to attacker-controlled servers via:
- HTTP/HTTPS requests: Data is uploaded to a malicious web server or even reputable file-sharing APIs.
- FTP transfers: Files are sent to an attacker’s FTP server.
- Email: Sensitive info is emailed directly to the attacker.
4. Data Distribution: Fueling the Cybercrime Economy
Once collected, your data is packaged into “logs” and sold on underground marketplaces or Telegram bots. Centralized markets like the now-defunct Genesis marketplace or decentralized platforms like Russian Market offer stolen credentials for as little as $10 per log. Popular targets include accounts from Google, Facebook, Roblox, Microsoft, and Instagram, with gamers being particularly vulnerable due to less stringent security practices.
Initial Access Brokers (IABs) buy these logs, identify valuable targets (like corporate network access), and resell them to ransomware gangs or other cybercriminals. This ecosystem, powered by MaaS platforms like RedLine, LummaC2, StealC, and Vidar, makes infostealers a gateway to larger attacks like ransomware or financial fraud.
5. Further Criminal Activity
The stolen data fuels a range of malicious activities:
- Identity theft: Impersonating you to open accounts or make purchases.
- Financial fraud: Draining bank accounts or crypto wallets.
- Phishing: Crafting targeted attacks using your stolen contacts.
- Ransomware: Using stolen credentials to breach networks, as seen in the 2024 Snowflake breach affecting 165+ organizations.
- Sextortion/blackmail: Threatening to expose sensitive files or communications.
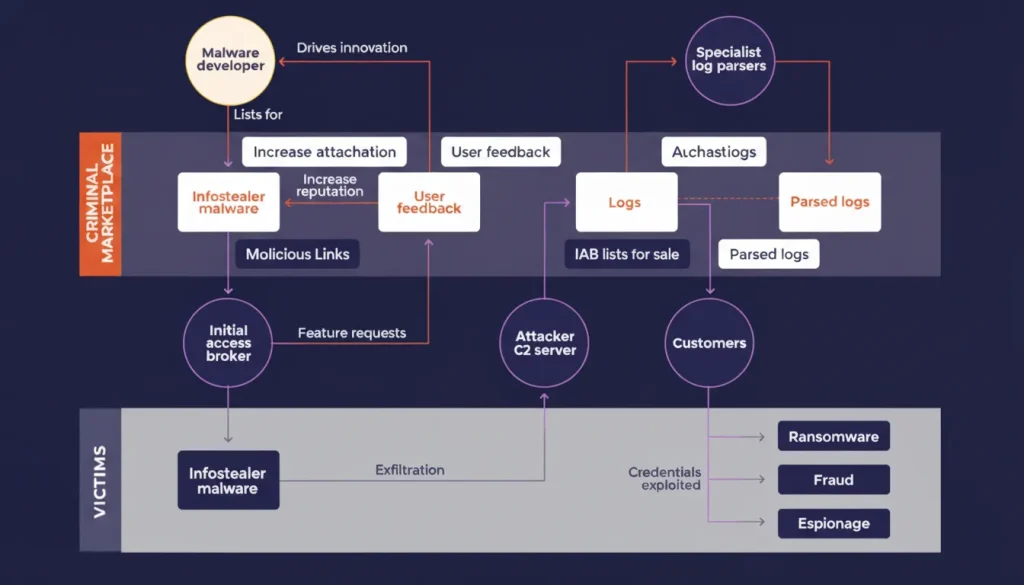
The Infostealer Economy (MaaS → IAB → RaaS)
Infostealers are the backbone of a sophisticated cybercrime economy. The MaaS model has made them accessible to anyone with a few hundred dollars, lowering the technical barrier to entry.
Platforms like RedLine, LummaC2, StealC, and Vidar offer monthly subscriptions ($150-$250) that include technical support, updates, and dashboards for managing stolen data.
According to ESET’s H2 2024 Threat Report, Lumma Stealer saw a 369% increase in detections, while others, like RedLine, have been disrupted by law enforcement but quickly replaced by new variants.
The ecosystem is highly organized:
- Vendors develop and maintain infostealer tools, competing on log quality and speed of delivery.
- Affiliates buy licenses to run infection campaigns, harvesting data to sell or trade.
- Initial Access Brokers (IABs) purchase logs, identify valuable targets, and resell access to ransomware or fraud groups.
- Marketplaces (e.g., Russian Market, Telegram bots) facilitate the sale of logs, often for as little as $10 per log.
This supply chain thrives on speed. Fresh logs, especially those with valid session tokens, are most valuable because security teams can quickly patch vulnerabilities or revoke access. The 2024 Snowflake breach, for instance, was linked to infostealer logs, highlighting how these attacks enable larger breaches.
Geographic Trends: Data from Russian markets shows significant log volumes from countries like India, Brazil, and Indonesia, reflecting the global reach of infostealer campaigns. Gamers are a prime target due to their frequent use of unverified mods or cheats, which often hide malware.
Why cookies and tokens are the crown jewels
Most people think, “I use MFA; I’m safe.” Infostealers target the post‑login reality: if the malware can steal session cookies (or OAuth refresh tokens), an attacker can impersonate your active session without your password or second factor. That’s why:
- Revoking sessions and forcing re‑authentication is critical after an incident.
- Shorter session lifetimes, device binding, and token replay detection matter more than ever.
- Phishing‑resistant MFA (FIDO2/passkeys) is superior to SMS/OTP, but you still need session management—passkeys don’t protect a stolen cookie.
Are infostealer logs always “true”?
Investigators often find noise in stealer datasets:
- User error: mistyped emails or credentials get captured and later misattributed.
- Criminals get infected too: operators testing credential lists on their own compromised machines produce logs that make it look like thousands of people are freshly compromised, when it’s really old breach data being re‑checked.
- Partial/garbled captures: keyloggers miss characters, file harvesters skip formats, or uploads are truncated.
Bottom line: treat stealer logs as a strong signal to respond, but verify before assuming a fresh endpoint compromise.
How Infections Actually Start
- Phishing themes: unpaid invoices, shipping problems, job offers, fake legal notices, or “urgent security updates.” Many arrive as password‑protected archives with the password in the email to evade scanners.
- SEO poisoning: you search for “download [popular tool]” and a top result is a convincing fake domain with a signed but malicious installer.
- Compromised ads & social promos: hijacked brand accounts push “exclusive” offers that land on malware pages.
- Cracked games and mods: “free” cheats, bots, or texture packs often bundle stealers. (Gaming communities and Discords are frequent targets.)
- Mobile angles: sideloaded APKs, third‑party app stores, and fake wallet tools prey on Android/iOS users. While iOS is more locked down, account‑level theft still happens via session hijack if a Mac/PC in the ecosystem is infected.
Signals you might be infected
Unlike ransomware, most stealers try to be invisible. Still, you might notice:
- Unfamiliar processes that vanish quickly after startup
- A burst of outbound HTTPS traffic to random domains right after you open a browser
- New scheduled tasks or Run keys
- Antivirus suddenly disabled or exclusions quietly added
- Password reset emails or MFA push prompts you didn’t initiate
- Unrecognized logins to your accounts reported by providers
You usually won’t see pop‑ups bragging about “you’ve been hacked.” Silence is the feature.
How to Protect Yourself from Infostealers
Now, let’s get to the good stuff: how to keep your data safe. Here are steps you can take today to protect yourself from infostealers:
1. Use Robust Security Software
- Action: Install reputable antivirus or endpoint detection and response (EDR) software on all devices—PCs, Macs, and mobiles. Examples include Bitdefender, Malwarebytes, or ESET.
- Why: These tools use behavior and signature-based detection to catch infostealers before they can do harm.
- Pro tip: Keep your software updated to protect against the latest threats. ESET’s H2 2024 report noted a 369% surge in Lumma Stealer detections, so staying current is critical.
2. Be Phishing-Savvy
- Action: Avoid clicking links or opening attachments in unsolicited emails or texts. Verify the sender by contacting them through a trusted channel (e.g., call your bank to confirm an email).
- Why: Phishing is the top delivery method for infostealers. Tools like ProtonVPN’s NetShield can block known malicious links.
- Pro tip: Hover over email sender addresses to check for spoofing (e.g., “[email protected]” instead of “[email protected]”).
3. Download Software Safely
- Action: Only download apps or software from official stores like Google Play, Apple App Store, or trusted developer websites. Avoid pirated software or game mods.
- Why: Cracked software and mods, like those for Hamster Kombat, often hide infostealers like Lumma Stealer.
- Pro tip: Check app reviews and permissions before downloading. If an app requests excessive access (e.g., to your clipboard or files), it’s a red flag.
4. Keep Your System Updated
- Action: Regularly update your operating system, browsers, and apps to the latest versions.
- Why: Updates patch vulnerabilities that infostealers exploit, like outdated browser plugins.
- Pro tip: Enable automatic updates to stay protected without the hassle.
5. Strengthen Your Logins
- Action: Use a password manager (e.g., Proton Pass, Bitwarden) to create and store strong, unique passwords for every account. Enable MFA wherever possible.
- Why: Strong passwords and MFA reduce the impact of keylogging and credential theft, though session token theft can bypass MFA.
- Pro tip: Use a password manager with dark web monitoring (like Proton Pass) to get alerts if your credentials appear in stolen logs.
6. Clear Browser Data Regularly
- Action: Periodically clear cookies, cache, and saved form data from your browsers.
- Why: This minimizes the risk of session hijacking by reducing the data available to steal.
- Pro tip: Use browser extensions like uBlock Origin to block malvertising and trackers that could lead to infostealer infections.
7. Monitor Your Accounts
- Action: Set up activity alerts with your bank and other critical accounts. Regularly check for unrecognized logins or transactions.
- Why: Early detection can stop fraud before it escalates. Tools like Proton Sentinel can flag malicious login attempts.
- Pro tip: Use services with dark web monitoring to get notified if your data appears in infostealer logs.
8. Be Cautious on Social Media
- Action: Avoid clicking on ads or posts promising “too good to be true” deals, especially from unfamiliar accounts.
- Why: Social scams often lead to malicious websites or downloads that install infostealers.
- Pro tip: Google suspicious offers to check for scam reports before engaging.
9. Secure Your BYOD Environment
- Action: If you use personal devices for work, ensure they’re protected with EDR software and comply with your company’s security policies.
- Why: 70% of infostealer infections target personal devices, which can be entry points to corporate networks.
- Pro tip: Use separate browsers or profiles for work and personal activities to limit cross-contamination.
10. Educate Yourself and Others
- Action: Stay informed about cyber threats and share tips with friends and family.
- Why: Awareness is your first line of defense. Recognizing phishing or fake software prompts can stop infostealers before they start.
- Pro tip: Follow reputable cybersecurity blogs or accounts on X for real-time updates on threats like Lumma Stealer or Vidar.
The Enterprise Defense Stack
Infostealers are fundamentally an identity and session problem. Tools help, but policy and architecture win the long game.
Identity, access, and session controls
- Phishing‑resistant MFA by default (FIDO2/passkeys). Kill legacy auth (POP/IMAP/SMTP basic) and block SMS for admins.
- Short‑lived sessions with step‑up re‑auth for sensitive actions; enable continuous access evaluation where supported.
- Device binding for tokens (tie sessions to a cryptographic device fingerprint) and detect token replay.
- Conditional access: only allow SaaS access from compliant, managed devices.
Browser & data controls
- Disable browser password storage and sync for corporate accounts via policy (Chrome/Edge/Firefox enterprise policies).
- Isolate admin access: dedicate hardened browsers or jump hosts for admin consoles.
- Control extensions with allowlists; block crypto‑related extensions organization‑wide unless approved.
Endpoint and network
- EDR/XDR with behavioral rules for credential dumping, cookie theft, clipboard tampering, and suspicious browser DB access.
- Enable AMSI, Attack Surface Reduction rules (Windows), and application control/allowlisting for installers and scripts.
- DNS filtering + web proxy: block fresh domains, malware families, and known stealer C2s; enable TLS inspection where lawful.
Email & collaboration security
- Advanced phishing protection: attachment sandboxing, link rewriting, anomaly detection on supplier threads.
- Banners for external senders; enforced DMARC/DKIM/SPF alignment.
Monitoring & intel
- SIEM rules to correlate endpoints, identity, and network events around browser artifacts (e.g., access to Login Data, Cookies, or Chromium Local State).
- Dark‑web monitoring for stealer logs mentioning your domains and key user emails. Prioritize logs with fresh cookies/tokens.
BYOD & remote work
- Enforce device posture checks (disk encryption, OS version, EDR present) before granting access.
- Provide a VDI or browser‑isolation option so contractor/personal devices never hold long‑lived sessions.
Governance & training
- Security awareness with real, current examples (malvertising, AI‑tool impostors, fake game mods) and reward reporting.
- Clear software acquisition policy: no cracked software, and a fast path to request legit tools so employees aren’t tempted.
If You Think You’re Infected
Time matters because valid cookies are liquid gold for attackers. Here’s what to do, in order.
For individuals
- Go offline: disconnect the device from Wi‑Fi/ethernet. Don’t power off yet (you may lose volatile evidence), but stop the bleeding.
- Use a clean device (phone/tablet not logged into the same browser) to change passwords for email, bank, and key accounts. Turn on FIDO2/passkeys if supported.
- Revoke sessions/tokens:
- Google: Security › Your devices and Sign out of all sessions; review Third‑party access and remove unknown apps.
- Microsoft/Outlook: Sign‑out everywhere; reset App passwords; review OAuth consents.
- Apple ID, Facebook, Instagram, Discord, Slack, GitHub, Dropbox: sign out all, review authorized apps.
- Enable account alerts: login notifications, new device alerts, and transaction alerts with your bank.
- Scan the suspect device with a reputable AV/EDR. If it finds a stealer, quarantine and plan a full reinstall. Don’t trust “clean” after a single removal.
- Wipe and rebuild if possible. After rebuild, restore files from clean backups only.
- Rotate secrets used on that machine: passwords, recovery codes, API keys, SSH keys, and wallet keys. Assume autofill data was exposed.
- Financial safeguards: set up spending alerts, consider a credit freeze, and watch statements for weeks.
For teams (SOC runbook)
- Contain: isolate the host in EDR; block its egress at the firewall; snapshot the VM/drive if feasible.
- Triage artifacts: collect volatile data (process list, network connections), browser stores (Login Data, Cookies, Local State), and scheduler/autoruns entries. Hunt for common stealer drop paths in %AppData%, %LocalAppData%, ProgramData, temp, and suspicious scheduled tasks.
- Threat hunt across the fleet for the same indicators (hashes, C2 domains, mutexes, named pipes, command lines touching browser DBs).
- Identity response: force password resets; revoke all sessions for affected users; invalidate refresh tokens organization‑wide if needed. Review OAuth app grants and conditional‑access audit logs for unusual device IDs/locations.
- eDiscovery & logging: preserve evidence for legal/compliance. Tag the incident as identity compromise via stealer.
- Reimage compromised hosts. Consider golden image updates (latest patches, policies, and EDR).
- Communicate: notify impacted users, rotate shared credentials, and brief leadership on scope and business impact.
How browsers store secrets
- Chromium browsers (Chrome/Edge/Brave/Opera) store passwords in the Login Data SQLite DB and cookies in the Cookies DB. The AES key is kept in Local State and protected by DPAPI (Windows) or Keychain (macOS). Malware running as you can ask the OS to decrypt them. That’s why “but my cookies are encrypted” isn’t a defense against malware already on the host.
- Firefox uses key4.db and logins.json, with secrets guarded by the OS keystore or a master password when configured. If you never set a master password and malware runs in your session, decryption is easier.
- Token persistence: OAuth and SSO clients cache refresh tokens on disk; stealers grab those for long‑lived access even after a password change. Only token revocation (or short TTLs) fully cuts them off.
Practical tips: require a master password in your password manager, prompt for auth before autofill, and use separate browser profiles to reduce blast radius. For admins, enforce browser enterprise policies that block password saving and syncing with personal profiles.
Who Gets Targeted?
Broad campaigns target popular services because volume sells: Google, Microsoft, Facebook, Instagram, Roblox, Discord, and major game launchers are permanent best‑sellers in stealer markets. Gamers show up disproportionately because they’re lured by mods, cheats, and free premium builds, often installed on the same PCs used for school or work logins.
Tip: if you’re a parent or run a school network, treat game‑adjacent downloads like you would cracked office software: blocked by default with an easy, legit alternative path.
Common infostealer families you’ll hear about
- Lumma (a.k.a. LummaC2): fast development cadence, strong cookie/token focus, frequently delivered via malvertising and fake tools.
- RedLine: historically widespread MaaS; has seen disruptions but copies and forks persist.
- StealC / Raccoon / Vidar / Azorult: long‑running families targeting browser stores, wallets, Discord/Telegram tokens, and screenshots.
- Agent Tesla / LokiBot / TrickBot: often straddle the line between RATs and stealers; once they’re in, they can deploy additional payloads.
You don’t need to memorize names; the behavior—grabbing browser secrets and exfiltrating fast—is what matters.
Final Thoughts
Infostealers are the starting pistol for many modern breaches. They spread quietly, monetize quickly, and hand your accounts to someone who knows exactly what to do next.
The good news: you can raise the cost for attackers dramatically with practical steps—phishing‑resistant MFA, strict browser hygiene, strong session management, and managed devices. Whether you’re locking down a single laptop or a thousand, the formula is the same: reduce the ways in, shorten the time windows, and be ready to revoke and rotate fast.
Stay sharp, update often, and keep your identity—the keys, cookies, and credentials—where they belong: with you.
A distant cousin to the famous rogue operative and with all the same beliefs. I enjoy exposing unseen threats to your privacy and arming you with the knowledge and resources that it takes, to stay invisible in a world that’s always watching.
- Edword Snowenhttps://stealthkits.net/author/snowen/
- Edword Snowenhttps://stealthkits.net/author/snowen/
- Edword Snowenhttps://stealthkits.net/author/snowen/
- Edword Snowenhttps://stealthkits.net/author/snowen/

